PKI is an initialism for public key infrastructure. The context I typically see it used in are TLS or PGP. Don’t worry if you don’t know what those are. To understand PKI, you need to understand some basic cryptographic concepts. There is no math required. For a more complete introduction to cryptographic concepts, I wrote a guide several years ago.
If you are in a hurry and just want a simple definition, scroll down to the summary.
I will start with a brief overview of the concepts needed to understand PKI.
Cryptographic Concepts
In order to understand PKI, you need to understand asymmetric encryption and symmetric encryption, hashes, and signatures. I’ll keep the explanations simple.
For all intents and purposes, TV and movies are generally wrong about encryption. A super genius doesn’t just decrypt encrypted data in 5 minutes. Cryptography that is trusted by the security and cryptography communities couldn’t be broken in any reasonable amount of time using all of the computing resources of a large cloud provider.
Symmetric encryption is a way to protect data by taking the data, a key, and applying the encryption algorithm to the data. A key is essentially a small bit of random data of a fixed length. Common key sizes range from 256-4096 bits, depending on the algorithm. The same key is used to both encrypt and decrypt data. So all parties must keep the key secret or the encryption becomes worthless.
Asymmetric encryption also protects data, but two keys are used. Either key can encrypt or decrypt, but not both. One key is kept private, and the other is public. By public, I mean available to anyone and everyone. When you connect to this site with your browser, it literally sends you its public key as part of securing the connection. Anything encrypted with the public key can only be decrypted by the private key. Anything encrypted with the private key can only be decrypted by the public key.
Asymmetric encryption is much slower than symmetric. So when programs, like your web browser establish a secure connection, they only use asymmetric encryption to verify identities and agree on a private key. Your browser and web sites then use symmetric encryption to communicate. When your computer established and encrypted connection to tylersguides.com, it will generate a symmetric key and encrypt it with my public key. Since I am the only one that has my private key, I am the only one who can decrypt it. We then use that key and symmetric encryption to communicate. That is an oversimplification of course and not perfectly accurate, but it is close enough for understanding how PKI works.
A hash is an algorithm that takes an arbitrary amount of data and generates a fixed length output. For example, if I were to run a single character through a hashing algorithm with 128 bit output, the output would be 128 bits; if I were to feed it the entirety of the internet, the output is 128 bits. Cryptographic hashes are very resistant to collisions, or two inputs having the same output. Hashes are often used for password storage.
A Signature is when you create a hash of something and encrypt it with your private key. Signatures are used to verify the source of things.
So What is PKI then?
PKI is a system that facilitates exchanging of cryptographic keys and trust using cryptography. There is more than one PKI system.
A common PKI system is TLS using X.509 certificates issue via trusted certificate authorities. A certificate in this context is a bit of information, like the domain of a site (E.g. tylersguides.com), a validity period, where to validate its status, and in this case, a public key. TLS is a standard for establishing encrypted network connections over a potentially distrusted network, like the internet. A certificate authority is an organization that issues certificates.
These certificate authorities have asymmetric key pairs. They release their public keys to the public. Site operators like me send their information and public key (called a certificate signing request or CSR) to a certificate authority. The certificate authority has the operator prove that they are the real operator of the site and not an impersonator. They then create your certificate using your public key and the verified information and sign it with their private key. Anyone can verify the signature using the well known public key.
When you connect to something, like this site, that uses TLS and X.509 certificates, the site sends you its certificate. The certificate has the following information, the site identity (tylersguides.com), the issuing certificate authority, a validity period, how to verify that the certificate authority hasn’t revoked it (i.e. tells users not to trust it), and the authority’s signature. That isn’t exhaustive, but enough to understand the concept. Your browser then verifies all of that information, including the signature. Unless an attacker somehow was able to get the authority’s private key, which would be extremely difficult, you can be reasonably sure that the site you are connecting to is the real site.
You may be wondering how you know you can trust certificate authorities. Organizations that make software that uses TLS will include a bundle of certificate authority certificates with the software. The requirements authorities must meet to be trusted are stringent. Check out the links in the reference section if you would like to know more about this process.
Step by Step Example
Let’s go through a simplified version of the process of you using PKI to download this page using Mozilla Firefox. With the exceptions of installing Firefox and going to this page, the process is completely transparent and automatic from your perspective. I’ve left out quite a bit for the sake of simplicity. The purpose of this guide is to help you understand the concept of PKI, not the nitty gritty details of real life implementation.
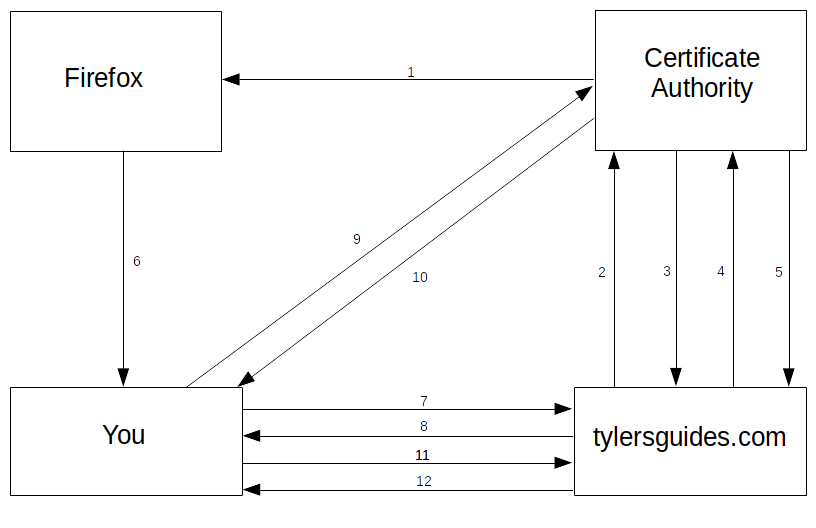
Simplified PKI Process.
- A certificate authority meets the requirements to be trusted by Mozilla Firefox and publishes their certificate. Mozilla adds it to its list of trusted authorities and distributes it as part of Firefox.
- tylersguides.com asks the authority for a certificate signed by them.
- The authority responds by requesting tylersguides.com prove that they are actually tylersguides.com making the request and not an imposter.
- tylersguides.com provides sufficient evidence that they are not an imposter.
- The authority sends tylersguides.com a certificate signed with the authority’s private key.
- You download and install Mozilla Firefox on your device. Remember, it includes a bundle of certificates from trusted authorities.
- You send a request to tylersguides.com to securely download this page.
- tylersguides.com responds by sending the certificate they obtained from the certificate authority.
- Firefox reads the certificate and checks the signature by using its own copy of the public key the certificate claims to be signed by and asks the authority itself if it is still valid.
- The authority confirms the validity of the certificate.
- You send tylersguides.com cryptographic details, including a symmetric key they can use to send you the requested information securely.
- Finally, you get the information requested.
Summary
Public Key Infrastructure is a system that facilitates the exchange and trust of cryptographic keys. I used TLS and X.509 certificates as an example. Trusted certificate authorities sign certificates that include identity information and a public key. People use these signatures to verify the public keys of who they communicate with. As long as the signature checks out, you can be reasonable sure you are not communicating with an imposter.
Other Sources
If you want more in depth information or alternative explanations, check out these sources:
References
These sources provide in depth technical details: